使用certbot-auto申请Let’s Encrypt Wildcard证书
Let's Encrypt 宣布ACME v2正式支持通配符证书,并将继续清除Web上采用HTTPS的障碍,让每个网站轻松获取管理证书,我们普通用户终于可以拥有免费Wildcard Certificate,俗称野卡.
通配型证书(wildcard certificate)是在一个域及其所有子域上应用的数字证书.通配型符号由一个星号和域名前的一段时间构成.安全套接层(SSL)证书常运用通配符来扩展子域的SSL加密.
通配符SSL证书可以同时保护一个域名下的2级子域名网站,比如*.yourdomain.com,对子域名网站是没有数量限制,用户可以随时添加自己的子域名网站.
ps:
为 *.yourdomain.com 域名申请的通配符证书不适用于 yourdomain.com ,如有需要则需要单独申请.
系统:centos 7(64位)
软件:certbot-auto
1.下载certbot-auto
wget https://dl.eff.org/certbot-auto
chmod +x certbot-auto
mv certbot-auto /usr/local/bin/
2.申请证书
certbot-auto certonly -d "*.slogra.com" --manual --preferred-challenges dns-01 --server https://acme-v02.api.letsencrypt.org/directory
ps:
申请通配符证书,只能使用 dns-01 的方式.
*.slogra.com 请根据自己的域名自行更改.
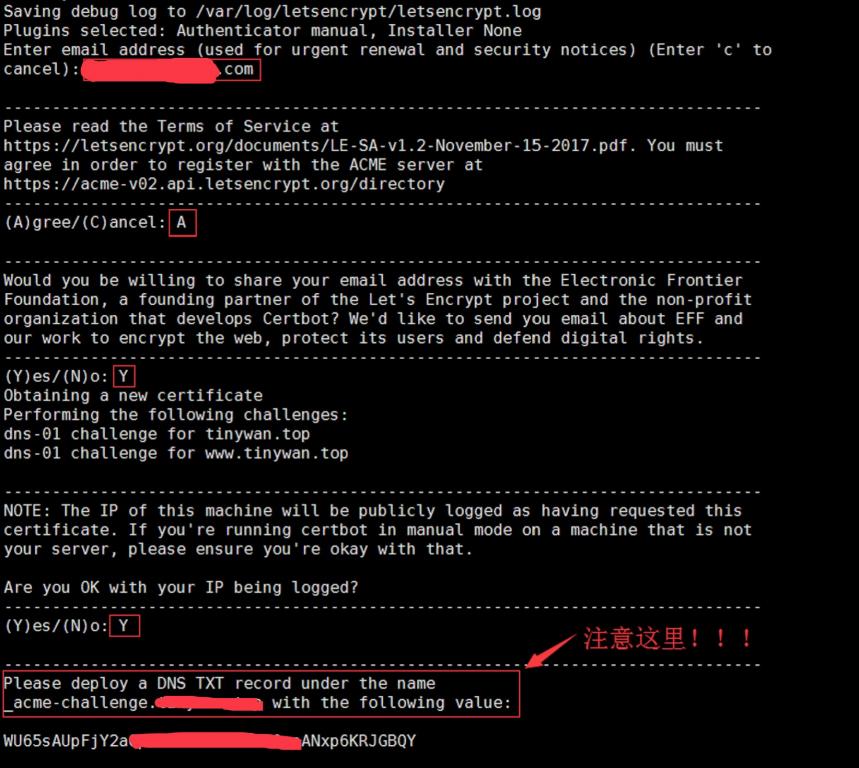
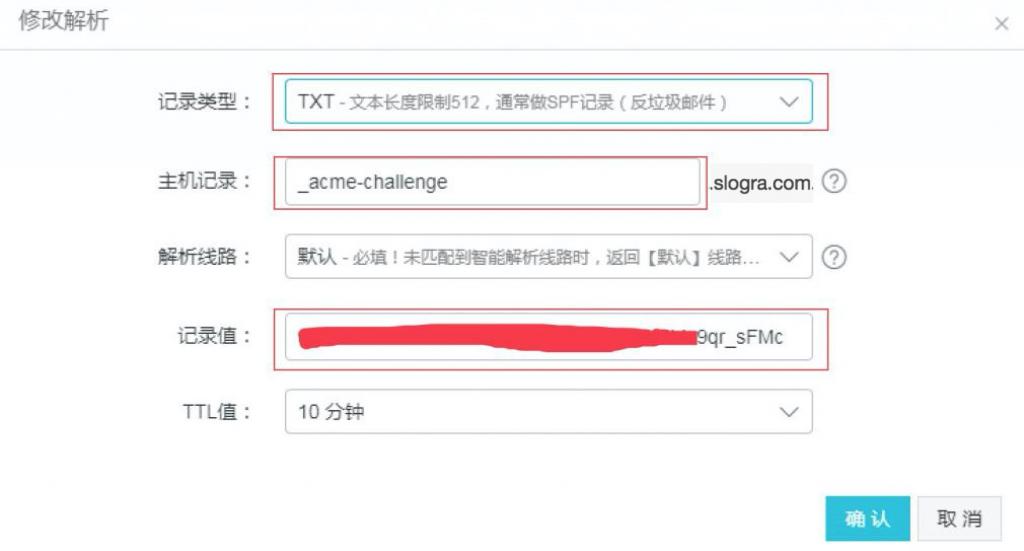
这里不要继续往下了申请通配符证书是要经过DNS认证的,按照提示,前往域名后台添加对应的DNS TXT记录,如下图:
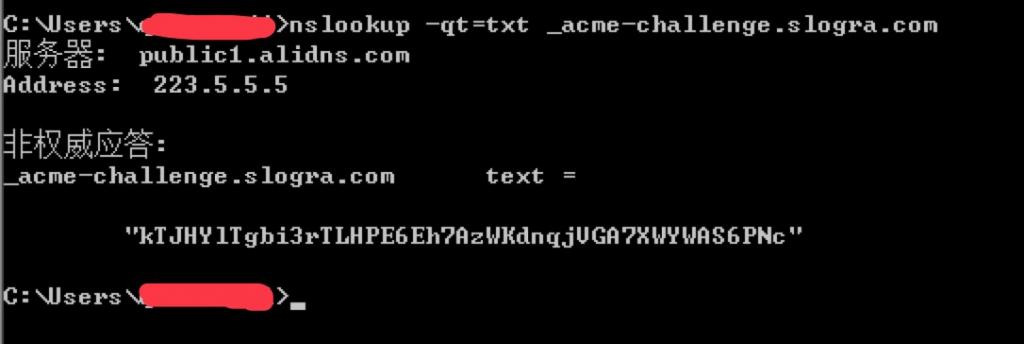
添加好后,我们要确认解析记录是否生效,执行以下命令:
dig -t txt _acme-challenge.slogra.com @223.5.5.5
windows系统在cmd里执行:
nslookup -qt=txt _acme-challenge.slogra.com
确认生效后,再回去回车继续执行,最后会输出如下内容:
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/xxx.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/xxx.com/privkey.pem
Your cert will expire on 2018-11-21. To obtain a new or tweaked
version of this certificate in the future, simply run certbot-auto
again. To non-interactively renew *all* of your certificates, run
"certbot-auto renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
证书存放位置在:
/etc/letsencrypt/live/xxx.com/
证书目录结构如下:
tree /etc/letsencrypt/live/xxx.com/
.
├── cert.pem
├── chain.pem
├── fullchain.pem
└── privkey.pem
好了,这样就说明证书已经申请下来了.接下来我要配置到nginx里.
3.nginx配置
server {
if ($host = blog.slogra.com) {
return 301 https://$host$request_uri;
}
listen 80;
server_name blog.slogra.com;
rewrite ^(.*) https://blog.slogra.com permanent;
}
server {
listen 443 ssl http2;
server_name blog.slogra.com;
ssl on;
ssl_certificate /etc/letsencrypt/live/slogra.com-0002/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/slogra.com-0002/privkey.pem; # managed by Certbot
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3;
ssl_ciphers "EECDH+CHACHA20 EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH+aRSA+RC4 EECDH EDH+aRSA RC4 !aNULL !eNULL !LOW !3DES !MD5 !EXP !PSK !SRP !DSS !RC4";
ssl_prefer_server_ciphers on;
add_header Strict-Transport-Security "max-age=63072000; includeSubdomains; preload";
add_header X-Xss-Protection 1;
....
}
最后就可以去浏览器上访问https://blog.slogra.com ,没有报错就可以了.



评论: