linux幽灵漏洞检测和修复方法
没想到最近linux的漏洞越来越多了,上一次的bash漏洞没过去多久,又爆出了新的漏洞,名为"幽灵漏洞(GHOST)".当我一看到有新的漏洞时,马上为我所管的服务器都打上了最新补丁,glibc的漏洞估计存在了很久了,大部分的编译都依赖于他,所以造成影响很大.好了,废话不多说,先来说说怎么检测服务器是否存在漏洞吧.
1.检测漏洞方法一:
vi ghost_check.sh
检测命令:
./ghost_check.sh
检测结果如下图:
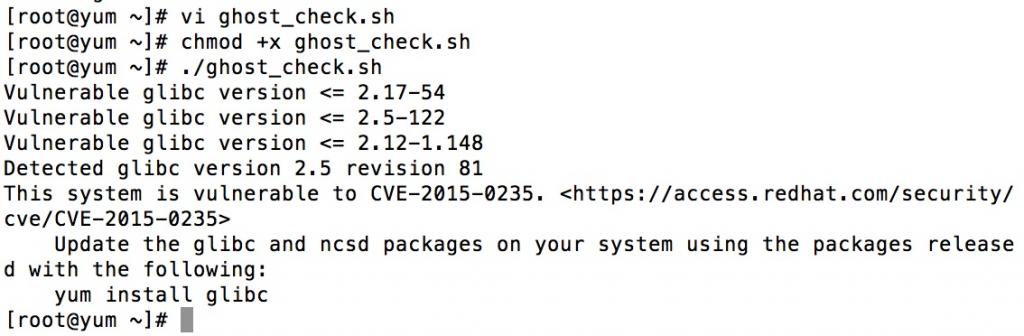
可以看到这台服务器是存在漏洞的.
2.检测漏洞方法二:
第2个检测方法在我的机器上报错,所以我用了其他人的图,如下:
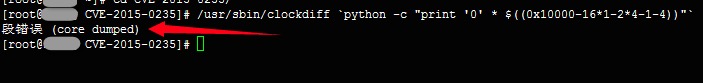
3.检测漏洞方法三:
vi ghost.c
检测命令:
gcc ghost.c -o ghost && ./ghost
检测结果如下图:
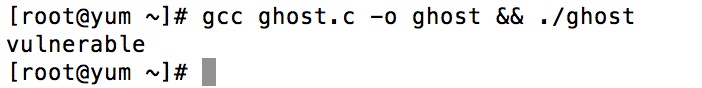
可以看到也是检测出了漏洞.好了,下面来说怎么修复漏洞吧.
4.修复方法:
RedHat、Fedora、CentOS系统:
yum update glibc glibc-devel glibc-common glibc-headers -y
Debian、Ubuntu系统:
apt-get clean && apt-get update && apt-get upgrade
或
apt-get clean && apt-get update && apt-get -y install libc6
ps:
升级后,建议重启用到glibc的进程或者重启服务器.
1.检测漏洞方法一:
vi ghost_check.sh
#!/bin/bash
vercomp () {
if [[ $1 == $2 ]]
then
return 0
fi
local IFS=.
local i ver1=($1) ver2=($2)
# fill empty fields in ver1 with zeros
for ((i=${#ver1[@]}; i<${#ver2[@]}; i++))
do
ver1[i]=0
done
for ((i=0; i<${#ver1[@]}; i++))
do
if [[ -z ${ver2[i]} ]]
then
# fill empty fields in ver2 with zeros
ver2[i]=0
fi
if ((10#${ver1[i]} > 10#${ver2[i]}))
then
return 1
fi
if ((10#${ver1[i]} < 10#${ver2[i]}))
then
return 2
fi
done
return 0
}
glibc_vulnerable_version=2.17
glibc_vulnerable_revision=54
glibc_vulnerable_version2=2.5
glibc_vulnerable_revision2=122
glibc_vulnerable_version3=2.12
glibc_vulnerable_revision3=148
echo "Vulnerable glibc version <=" $glibc_vulnerable_version"-"$glibc_vulnerable_revision
echo "Vulnerable glibc version <=" $glibc_vulnerable_version2"-"$glibc_vulnerable_revision2
echo "Vulnerable glibc version <=" $glibc_vulnerable_version3"-1."$glibc_vulnerable_revision3
glibc_version=$(rpm -q glibc | awk -F"[-.]" '{print $2"."$3}' | sort -u)
if [[ $glibc_version == $glibc_vulnerable_version3 ]]
then
glibc_revision=$(rpm -q glibc | awk -F"[-.]" '{print $5}' | sort -u)
else
glibc_revision=$(rpm -q glibc | awk -F"[-.]" '{print $4}' | sort -u)
fi
echo "Detected glibc version" $glibc_version" revision "$glibc_revision
vulnerable_text=$"This system is vulnerable to CVE-2015-0235. <https://access.redhat.com/security/cve/CVE-2015-0235>
Update the glibc and ncsd packages on your system using the packages released with the following:
yum install glibc"
if [[ $glibc_version == $glibc_vulnerable_version ]]
then
vercomp $glibc_vulnerable_revision $glibc_revision
elif [[ $glibc_version == $glibc_vulnerable_version2 ]]
then
vercomp $glibc_vulnerable_revision2 $glibc_revision
elif [[ $glibc_version == $glibc_vulnerable_version3 ]]
then
vercomp $glibc_vulnerable_revision3 $glibc_revision
else
vercomp $glibc_vulnerable_version $glibc_version
fi
case $? in
0) echo "$vulnerable_text";;
1) echo "$vulnerable_text";;
2) echo "Not Vulnerable.";;
esac检测命令:
./ghost_check.sh
检测结果如下图:

可以看到这台服务器是存在漏洞的.
2.检测漏洞方法二:
/usr/sbin/clockdiff `python -c "print '0' * $((0x10000-16*1-2*4-1-4))"`
第2个检测方法在我的机器上报错,所以我用了其他人的图,如下:

3.检测漏洞方法三:
vi ghost.c
#include <netdb.h>
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <errno.h>
#define CANARY "in_the_coal_mine"
struct {
char buffer[1024];
char canary[sizeof(CANARY)];
} temp = { "buffer", CANARY };
int main(void) {
struct hostent resbuf;
struct hostent *result;
int herrno;
int retval;
/*** strlen (name) = size_needed - sizeof (*host_addr) - sizeof (*h_addr_ptrs) - 1; ***/
size_t len = sizeof(temp.buffer) - 16*sizeof(unsigned char) - 2*sizeof(char *) - 1;
char name[sizeof(temp.buffer)];
memset(name, '0', len);
name[len] = '\0';
retval = gethostbyname_r(name, &resbuf, temp.buffer, sizeof(temp.buffer), &result, &herrno);
if (strcmp(temp.canary, CANARY) != 0) {
puts("vulnerable");
exit(EXIT_SUCCESS);
}
if (retval == ERANGE) {
puts("not vulnerable");
exit(EXIT_SUCCESS);
}
puts("should not happen");
exit(EXIT_FAILURE);
}检测命令:
gcc ghost.c -o ghost && ./ghost
检测结果如下图:

可以看到也是检测出了漏洞.好了,下面来说怎么修复漏洞吧.
4.修复方法:
RedHat、Fedora、CentOS系统:
yum update glibc glibc-devel glibc-common glibc-headers -y
Debian、Ubuntu系统:
apt-get clean && apt-get update && apt-get upgrade
或
apt-get clean && apt-get update && apt-get -y install libc6
ps:
升级后,建议重启用到glibc的进程或者重启服务器.


wget http://www.antian365.com/lab/linux0day/ghost.c
wget -O ghost_check.sh http://www.antian365.com/lab/linux0day/GHOST-test.sh.txt